Hashing Basics Explained
Understanding hashing
Welcome crypto dummiez!
This substack is focused on educating those of you that know nothing about crypto and blockchain technology.
If that’s you, then you’re in the right place!
Today’s topic? Hashing.
So what is hashing?
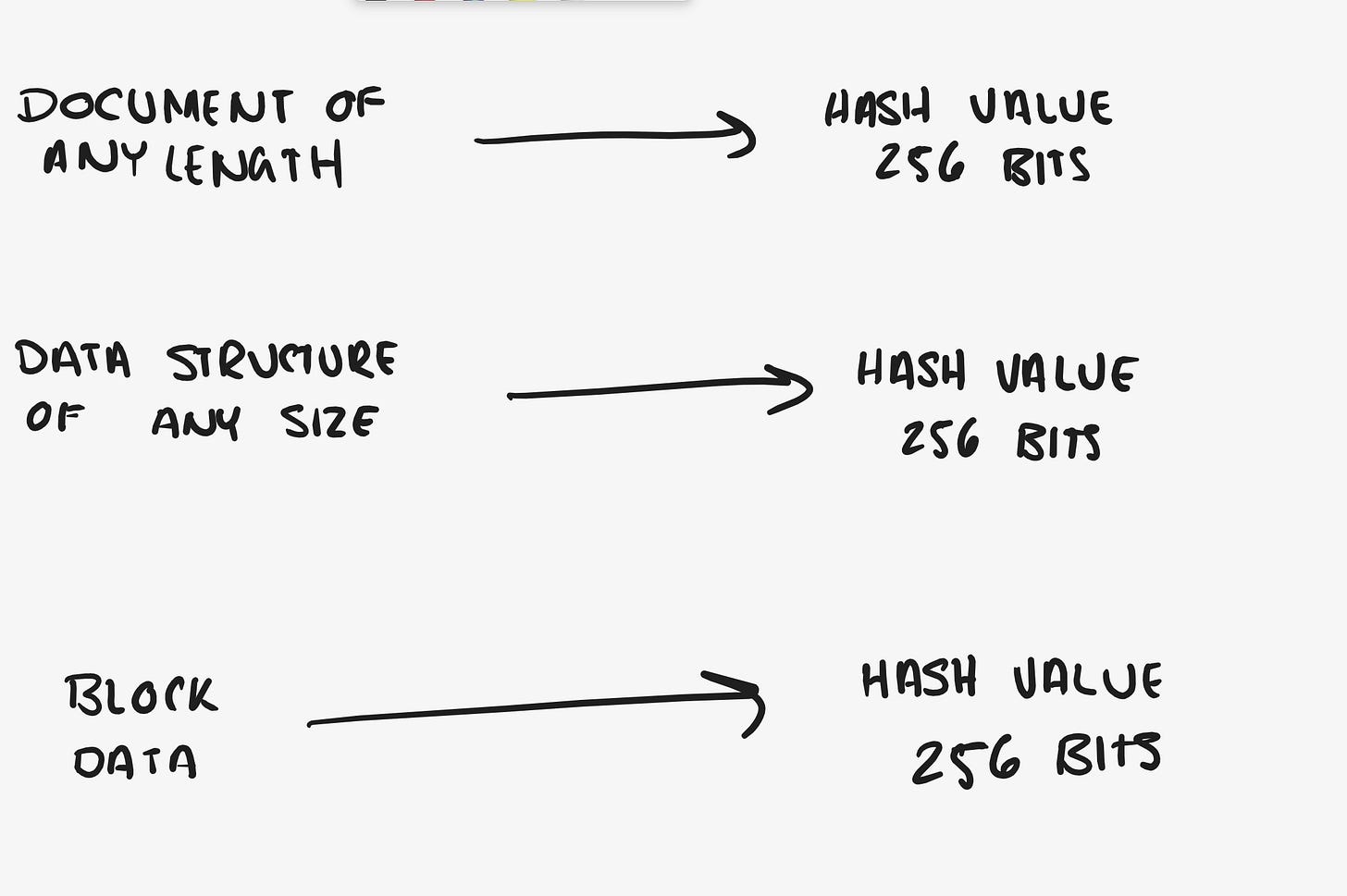
In it’s simplest form, hashing is generating a value from a string of text using a mathematical function. Essentially a hash function/hashing transforms and maps an arbitrary length of input data, to a unique fixed length value.
Below is a quick visual to help you understand.
The hash value is the output string generated by the hash function.
Hash values are stored in the form of (key, value) pairs on a hash table. The key (generated by the hash function) is used to identify the data.
The most common hash functions are:
SHA-3
SHA-256
KECCAK-256
Hash Requirements
Algorithms should be one-way functions and collision free. Ensuring no one can derive the original items from the hash value, and making sure the hash value uniquely represents the original items hashed. This is achieved through a strong algorithm (secure hash) and using the appropriate number of bits.
The most common being: 256 bits
A 256BIT hash value space represents: 2 to the power of 256 possible value combinations. (approx. 10 to the power of 77!)
Simple Hashing +Merkle Tree Hashing
With Simple Hashing:
All data items are linearly arranged and then hashed
Merkle Tree
Data is at leaf nodes of tree
Leaves are pairwise hashed to arrive at the same hash value as a simple hash
Below are some diagrams to help paint the picture.
EX: Simple Hash
EX: Merkle Tree
When is simple hash used?
Simple hash is used when a fixed number of items need to be hashed (ex: block header), and for verifying composite block integrity (not individual item integrity)
When is Merkle Tree used?
Merkle tree is used most commonly when the number of items vary from block to block, such as :
TX Hash #
State Hash #
Receipt Hash #
Remember, state = variable.
State may be modified by smart contract execution and the result of a contract execution may be returned in a receipt.
Hashing is used for account addresses, digital signatures, transaction hashes, state hashes, receipt hashes and block header hashes.
Conclusion: Hashing is used to help us efficiently find or store an item within a collection. In the case of the crypto universe, it is designed to identify users, locate transactions on a block, and verify receipts and digital signatures. It is a key component to blockchain technology and the infrastructure that is built on establishing trust amongst unknown peers.
Now you know some of the basics of Hashing!
You are one step closer to #GMI (Gonna Make it).
Next week we’ll follow up with our beginner’s guide!
We’ve covered setting up your first wallet, buying your first coins, initiating your first swap and providing liquidity.
On the next post we will briefly dive into NFT’s, accessing NFT marketplaces, creating your own (for all the artists that known nothing), and selling/listing artwork for sale.
Hope to see all you crypto dummiez next week!